'업무이야기 > Security' 카테고리의 다른 글
| Juniper SRX(방화벽) 패스워드 초기화 (5) | 2024.10.24 |
|---|---|
| DeepFinder (웹방화벽) (6) | 2024.10.23 |
| FortiGate SIP Debug (1) | 2023.05.02 |
| SRX IPSec Tunnel Sample (0) | 2023.05.02 |
| AhnLab Network Solutions (0) | 2022.11.21 |
| Juniper SRX(방화벽) 패스워드 초기화 (5) | 2024.10.24 |
|---|---|
| DeepFinder (웹방화벽) (6) | 2024.10.23 |
| FortiGate SIP Debug (1) | 2023.05.02 |
| SRX IPSec Tunnel Sample (0) | 2023.05.02 |
| AhnLab Network Solutions (0) | 2022.11.21 |
# Windows Server 2016의 AD를 사용

# FortiGate 200D v6.0.14build0457(GA) 사용
# Security Fabric/Fabric Connectors

# 사용자 또는 그룹을 선택

# User & Device\User Group 추가


# FortiGate Policy
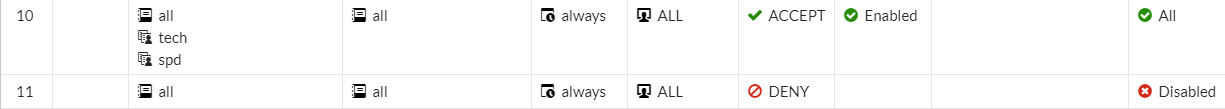
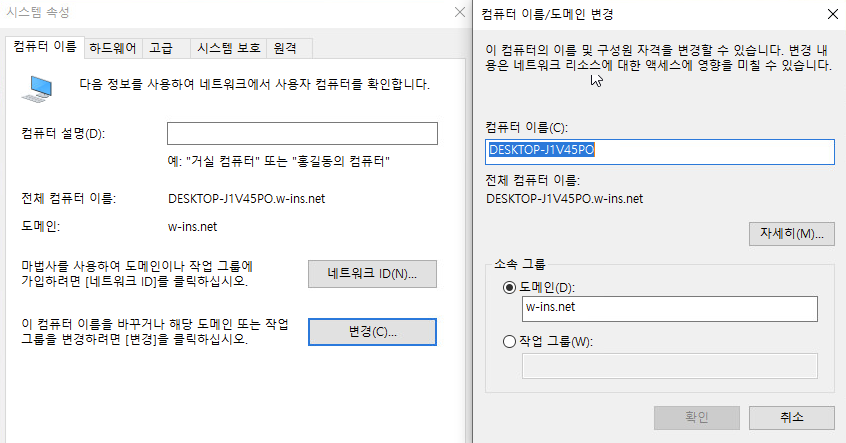
# Client OS에서 도메인을 통한 로그인 설정
# FortiGate에서 도메인을 통한 로그인 확인
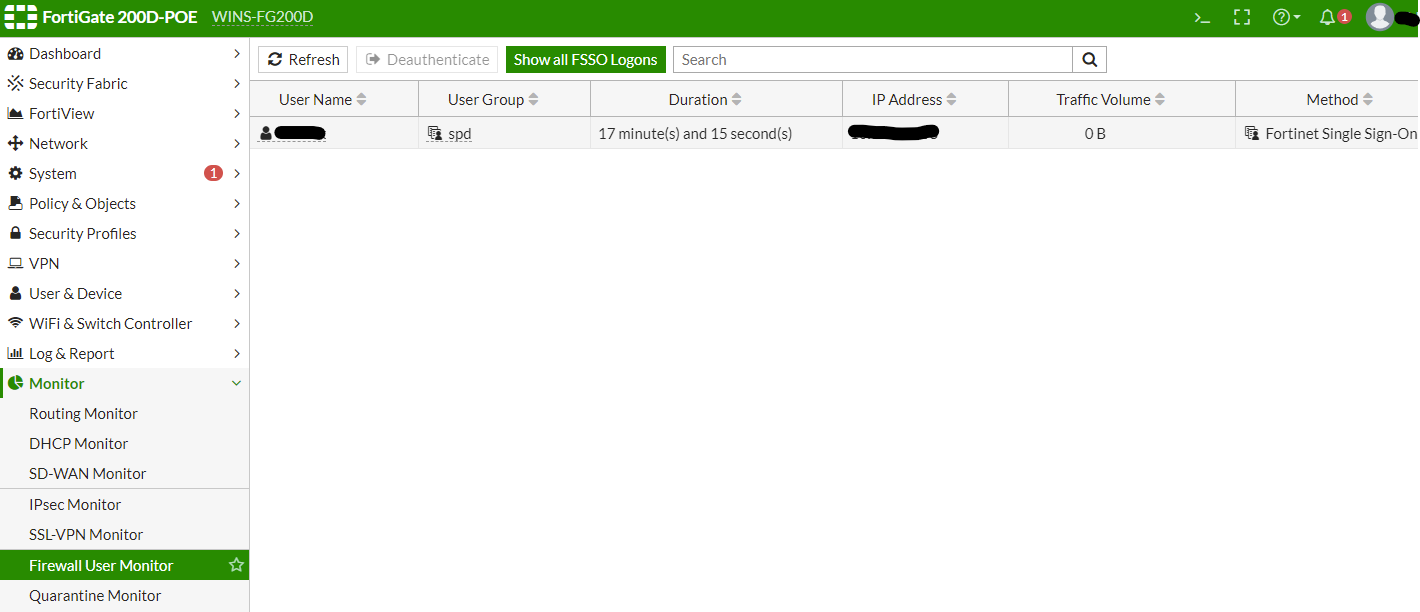
# 정책 테스트
| SRX IPSec Tunnel Sample (0) | 2023.05.02 |
|---|---|
| AhnLab Network Solutions (0) | 2022.11.21 |
| Juniper SRX Cluster configuration (2) | 2021.08.26 |
| Juniper SRX Policy-Based IPSec VPN (0) | 2021.08.26 |
| Juniper SRX Routed-Based IPSec VPN (0) | 2021.08.26 |
FortiSandbox Shell mode
Then in cli, run 'fnsysctl shell', login with 'fsa_support/Support@FSA1’
reset-bulidno
Please provide me more information as below ;
2-1. CLI of "sandbox-jobs-move -p -j[JOB ID]". It is example as below ;
Step1> # sandbox-jobs-move -p -j3429900306737006651
/Storage/clean/20170710/00/2754/3429900306737006651
Step2> #tar -czvf j3429900306737006651.gz /Storage/clean/20170710/00/2754/3429900306737006651
Step3> #cp j3429900306737006651.gz /web/static/
Step4> On web browser, https://FSA_IP/static/j3429900306737006651.gz
2-2. CLI of " cp /ramdisk/FortiSandboxGUI.db /web/static/"
Step1> On web browser, https://FSA_IP/static/FortiSandboxGUI.db
So, please export 6 job ID files and 1 fortisandboxGUI.db file and attach these files in this case.
| Configuration Example – Site-to-site VPN between SRX and Cisco ASA (Policy-based VPN) (0) | 2021.03.16 |
|---|---|
| MonitorAPP 웹방화벽 동작 체크 방법 (0) | 2021.01.29 |
| Fortinet FortiSandbox Clustering Setting sample (0) | 2021.01.20 |
| Juniper SRX 설정 방법 (CLI) (0) | 2021.01.20 |
| Axgate [SSL VPN] Configuration (5) | 2021.01.17 |
[FortiSandbox Clustering Setting]
Step 1 - Configure the master
Step 2 - Configure the primary slave
Step 3 - Configure the normal slave
| MonitorAPP 웹방화벽 동작 체크 방법 (0) | 2021.01.29 |
|---|---|
| Fortinet FortiSandbox Shell mode (0) | 2021.01.20 |
| Juniper SRX 설정 방법 (CLI) (0) | 2021.01.20 |
| Axgate [SSL VPN] Configuration (5) | 2021.01.17 |
| Juniper Firewall Transparent mode config (Example) (0) | 2018.05.08 |
Fortinet euc-kr 한글 지원 설정
CLI>
config system appearance
set fallback-charset EUC-KR
end
Spam Score 96 설정
CLI>
config antispam deepheader-analysis
set confiddence 96.000000
set greyscale-level 7
end
| FortiSandbox Clustering Setting (0) | 2017.08.08 |
|---|---|
| FortiSandbox Custom VM (0) | 2017.08.08 |
| Fortigate Port Restricted (0) | 2015.12.28 |
| Spam test (0) | 2015.12.28 |
| Fortigate SIP ALG / Fortinet SIP ALG (0) | 2015.12.28 |
| Fortigate IPS DoS configuration Sample (0) | 2013.03.10 |
|---|---|
| Fortigate Port Restricted (0) | 2013.03.10 |
| FortiOS 5.0 Enhancement Summary (0) | 2012.10.23 |
| Introducing FortiOS 5.0 - More Security, More Control, More Intelligence (0) | 2012.10.23 |
| WEBFRONT SSH PORT 변경 (0) | 2012.10.18 |
| Fortigate Port Restricted (0) | 2013.03.10 |
|---|---|
| Resetting a lost Fortigate Admin Password (1) | 2012.11.07 |
| Introducing FortiOS 5.0 - More Security, More Control, More Intelligence (0) | 2012.10.23 |
| WEBFRONT SSH PORT 변경 (0) | 2012.10.18 |
| Setting up a Policy-Based VPN Tunnel (0) | 2012.10.18 |
| Resetting a lost Fortigate Admin Password (1) | 2012.11.07 |
|---|---|
| FortiOS 5.0 Enhancement Summary (0) | 2012.10.23 |
| WEBFRONT SSH PORT 변경 (0) | 2012.10.18 |
| Setting up a Policy-Based VPN Tunnel (0) | 2012.10.18 |
| Fortigate IPS DoS Test용 configuration Sample (0) | 2012.10.18 |