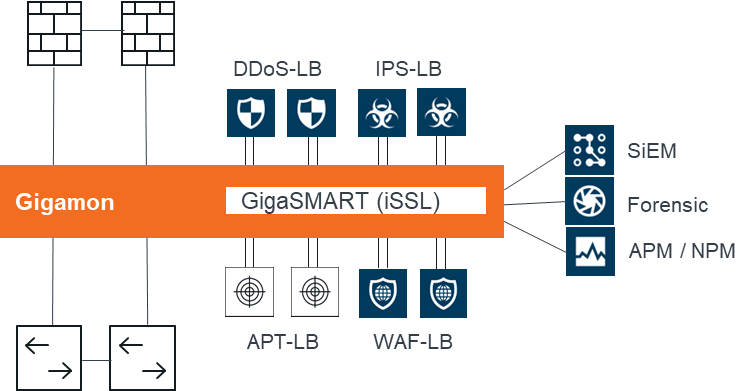
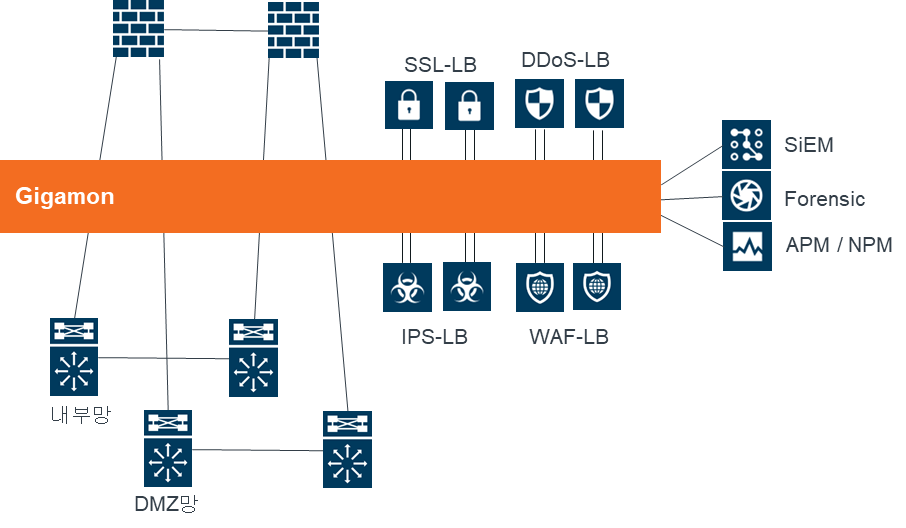
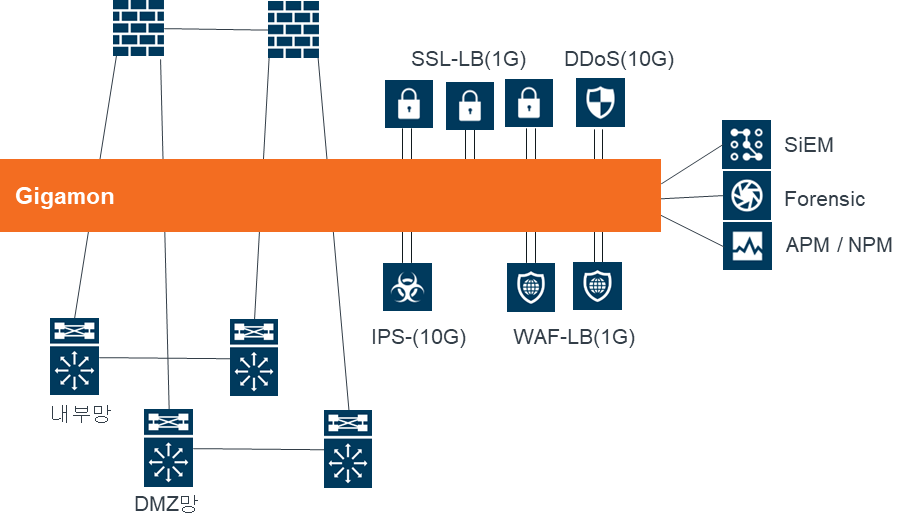
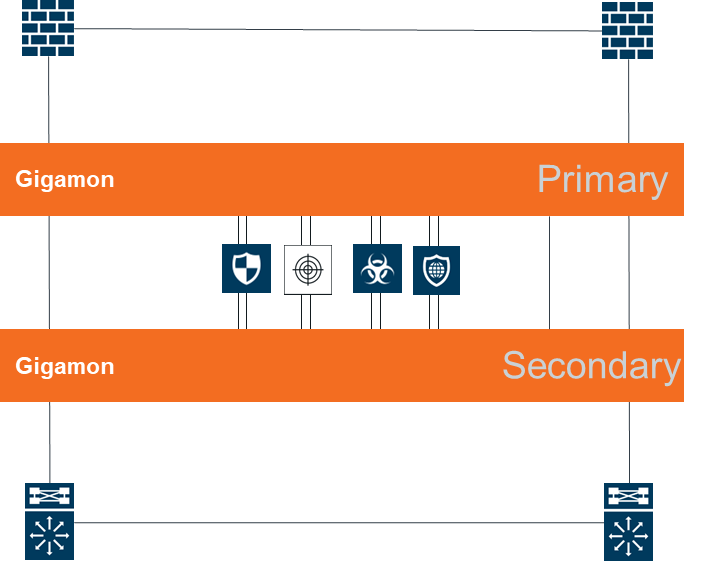
Gigamon에서 PCAP을 설정하기 위해서는 tx 또는 rx에 따라 1가지 옵션이 상이하다.
1. TX 기준
pcap alias iN1_a_tx
port 1/3/x17 tx
channel-port 1/3/x11
packet-limit 2000
filter ipdst 211.211.195.80 /32
exit
2. RX 기준
pcap alias iN1_a_rx
port 1/3/x17 rx
packet-limit 2000
filter ipdst 211.211.195.80 /32
exit
PCAP 을 완료 하기 위해 반듯이 아래 명령어로 PCAP을 중지 하기 바랍니다.
# no pcap all
'업무이야기 > 패킷전달플랫폼' 카테고리의 다른 글
| Gigamon RestAPI를 통한 VxLan Tunnel 생성 (1) | 2025.04.23 |
|---|---|
| Gigamon을 통한 구성 사례 (2) | 2024.11.07 |
| SSL VA PoC용 Gigamon Config (3) | 2024.11.06 |
| GigaVUE-FM Firmware upgrade 시 발생될 수 있는 문제점 (5) | 2024.10.29 |
| Gigamon Source port labeling (31) | 2024.10.04 |